Posted on: August 5, 2024 | Reading time: 10 minutes | Word count: 1981 words | Author: Dang Duong Minh Nhat
In the digital age, chat applications like Zalo and Telegram are essential tools for communication. However, they also open doors for cybercriminals to exploit users. One sophisticated method involves extracting IP addresses using spoofed URLs and phishing tactics. This blog post dives into the mechanics of URL spoofing, the common types of attacks, and a step-by-step demonstration of how attackers can track IP addresses through seemingly harmless interactions on these chat applications.
I’ll also explore a specific vulnerability in Telegram that allows hackers to discover a user’s IP address during calls, revealing the potential risks and the necessary precautions to safeguard your online privacy.
Table of Contents
- Table of Contents
- Tracking IP Address by using an Image URL
- Discover the user’s IP address using Telegram.
- Conclusion
- References
- Connect with Me
Tracking IP Address by using an Image URL
Background
URL spoofing
Definition of URL Spoofing
- URL Spoofing: URL spoofing involves creating a fraudulent link that appears to be from a legitimate source. This deceptive tactic aims to trick users into providing personal data or inadvertently downloading malware.
- Consequences: Interacting with spoofed URLs can result in the installation of malicious software or the unauthorized collection of sensitive information, such as passwords, financial details, and personal identification.
Distribution of Spoofed URLs Through Phishing: Spoofed URLs are often disseminated via phishing attacks. Phishing involves sending deceptive emails or text messages that lure recipients into clicking on fraudulent links. These messages often include enticing offers or urgent requests to prompt immediate action.
Common Types of URL Spoofing Attacks
- Links Behind Buttons or Words: A common phishing tactic involves embedding malicious links within buttons or hyperlinked text in emails that appear to be from trusted sources. By disguising the link, attackers can redirect users to harmful websites. Users can identify these links by hovering over them to reveal the true URL. Example: An email from a purported airline might offer discounted flights with a “Book Now” button. Clicking the button could lead to a malicious site that installs malware on the user’s device.
- Misspelled Links: Hackers often create URLs that closely resemble legitimate ones, altering only a single character. This method exploits users’ tendency to skim read, making it easy to overlook minor discrepancies. Example: A phishing email from a fake Netflix account may request confirmation of payment details, linking to “netfliix.com” or “n3tflix.com” instead of the official Netflix site.
- URL Shorteners: URL shortening services (e.g., bit.ly) are used to condense long URLs, making them easier to share. However, these shortened links obscure the destination URL, allowing attackers to mask malicious links. Example: A shortened URL shared on social media or via text message may lead unsuspecting users to harmful websites.
- Links with Non-Latin Characters: Hackers exploit non-Latin characters to create URLs that look nearly identical to legitimate ones. This method, known as homograph attack, involves using characters from different alphabets that appear similar to Latin characters. Example: A spoofed URL like “ņordvpn.com” may appear to be the legitimate “nordvpn.com” at a quick glance, deceiving users into visiting a fraudulent site.
Phishing
Phishing is a type of cyber-attack where attackers impersonate a trusted entity to deceive users into providing personal information. Commonly, cybercriminals masquerade as banks, online transaction websites, e-wallets, or credit card companies to trick users into sharing sensitive information, such as login credentials, transaction passwords, credit card details, and other valuable data.
Typically, phishing attacks are executed via emails and text messages. When users open these emails and click on the spoofed links, they are directed to a fake login page where they are prompted to enter their credentials. If they fall for the scam, the attackers immediately gain access to their information. In this case, I will focus on the use of phishing to distribute URL spoofing attacks.
Proof of Concept
Attack Scenario
In this section, I will outline a detailed attack scenario demonstrating the use of URL spoofing to track the IP addresses of victims through various interactions on chat applications like Zalo and Telegram.
Step 1: Creation of a Spoofed URL. Select an image to use as bait. This image could be a popular meme, an interesting photograph, or a seemingly important document that the attacker believes will entice the victim to click the link. Upload the selected image to a website that allows for IP logging, such as Grabify, IP Logger, or a similar service. These services generate a URL that captures the IP address of the visitor when clicked.
Step 2: URL Shortening. Use a URL shortening service like Bitly or TinyURL to condense the lengthy IP logging URL into a shorter, more innocuous-looking link. Obtain the shortened URL, which will be less suspicious and more likely to be clicked by the victim.
Step 3: Distribution of the Spoofed URL. Craft a message to send to the victim through a chat application like Zalo or Telegram. The message should be compelling enough to encourage the victim to click the link. Send the message with the shortened URL to the victim via the chosen chat application.
Step 4: Tracking the IP Address. When the victim clicks on the shortened URL, they are redirected to the IP logging service, which records their IP address before displaying the image. Log in to the IP logging service to view the captured IP address and other relevant information about the victim’s device and location.
Exploitation Demo
Step 1: Creation of a Spoofed URL. Start by uploading the image to an image hosting website such as ImgBB. For this demonstration, I will use the link to the image. To track the IP address, I will use a service that logs and tracks IP addresses. Many websites offer logging services, but for this demo, I will use Grabify. Grabify allows us to log and track IP addresses and provide additional information about our target, such as the browser and operating system used. While Grabify offers both free and paid services, I will use the free package for this demonstration. Go to the Grabify website and enter the link to our online hosted image into the provided field. Click on the “Create URL” button to generate a tracking link.

A screen will pop up requesting you to agree to the terms of service and privacy policy. Make sure to read through the terms to ensure compliance with legal requirements. Accept the terms and continue to proceed with the creation of the tracking URL.
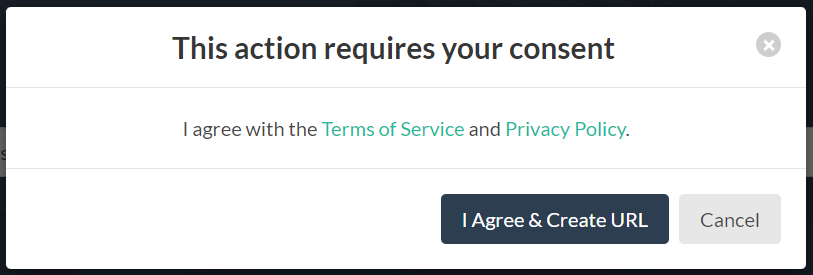
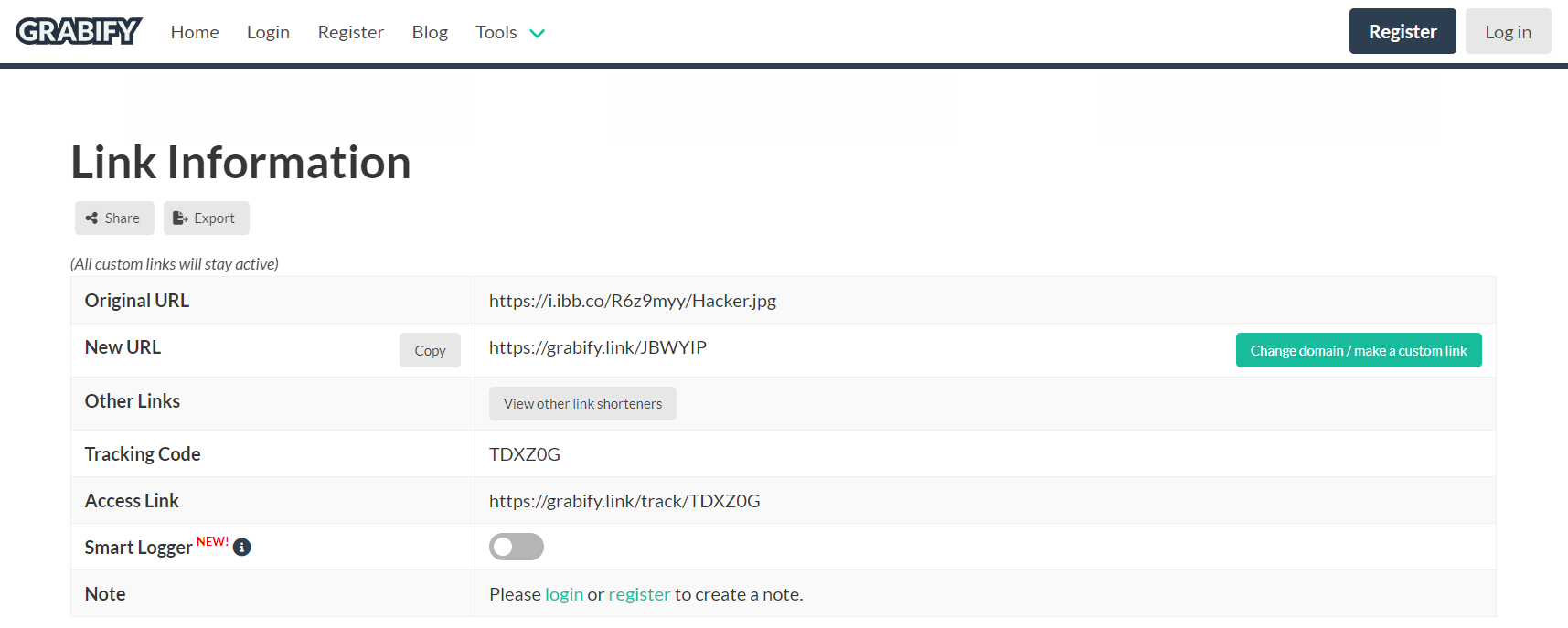
On this page I have several types of information to help us track IP address:
- Original URL - This is the original URL to your image on the website it is hosted on.
- New URL - This is the URL which I will send to our target in order to obtain information to help us track the IP address.
- Access Link - This is the link I will be using to access the information already logged onto our grabify platform.
Step 2: URL Shortening. After creating the tracking link with Grabify, you will have a URL that can be used to track the IP address of the target. However, this link can be identified as an information-fetching link, potentially raising suspicion. To make the link less detectable and more likely to be clicked by the target, I will use a URL shortening service. This service will convert the lengthy and potentially suspicious link into a shorter and more inconspicuous one. For this demonstration, I will use Bitly, a popular free URL shortening service.
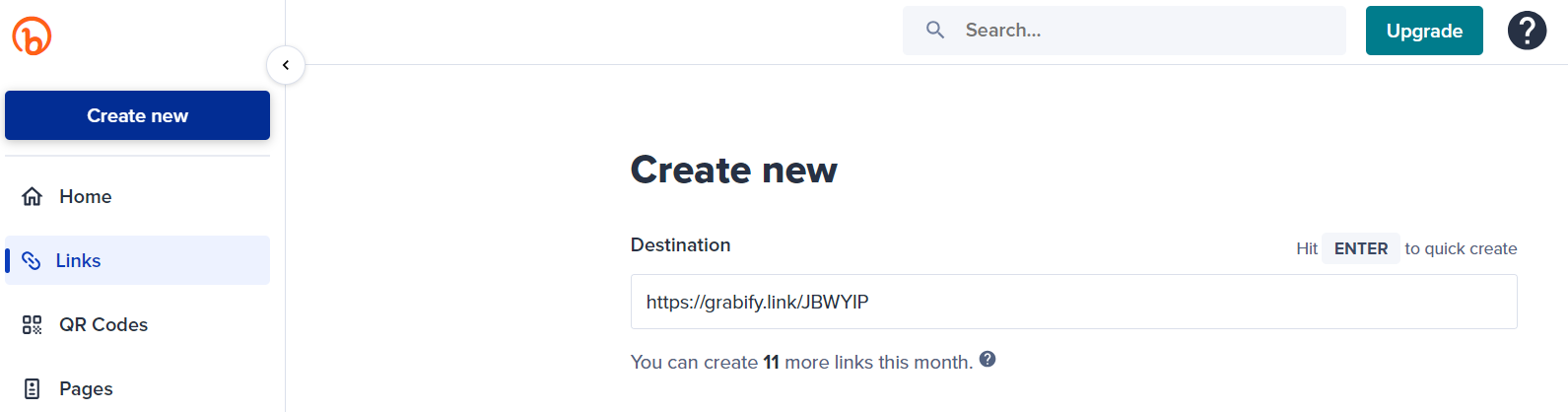
Visit the Bitly website and enter the Grabify tracking link into the URL shortening field. Click “Enter” to generate a shortened URL. For this example, the shortened URL is: https://bit.ly/4dtLE3Y.
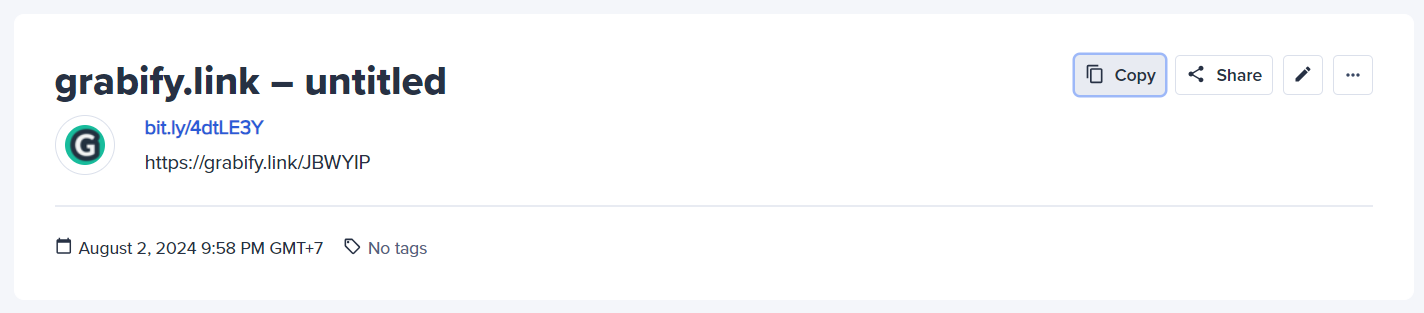
Step 3: Distribution of the Spoofed URL. Send message to Victim through Zalo with Spoofed URL.

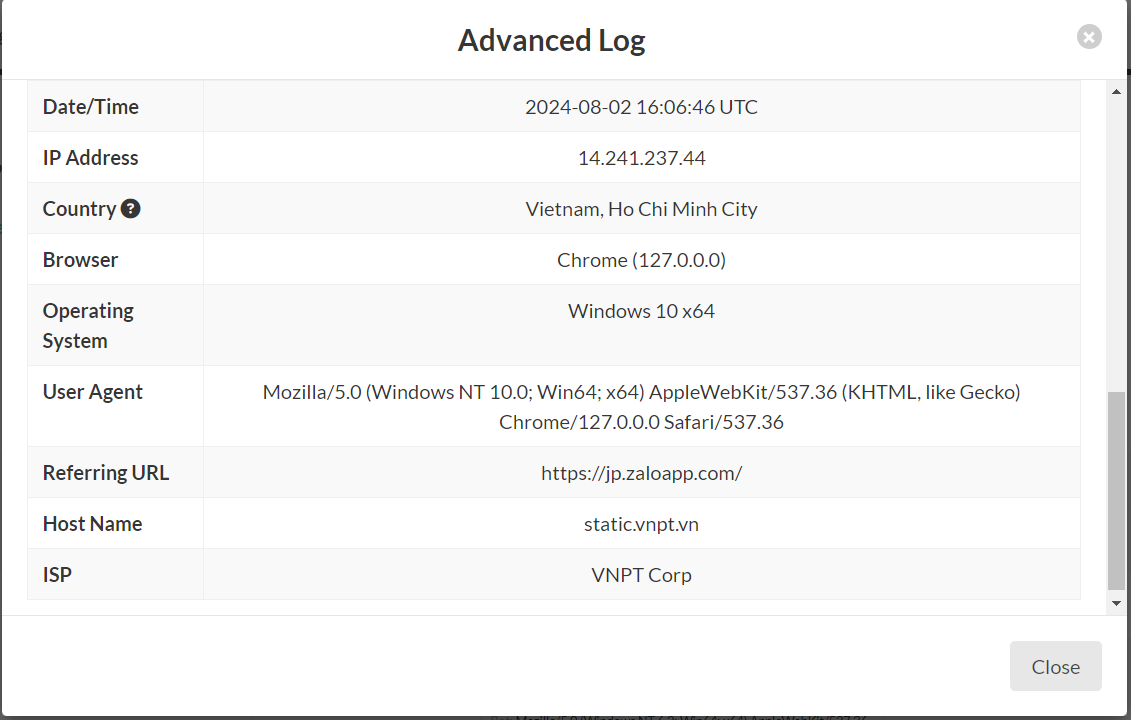
Step 4: Tracking the IP Address. Use Grabify to log and track IP addresses and provide additional information about our target. See the log results on the statistics table and its referring URL from Zalo.
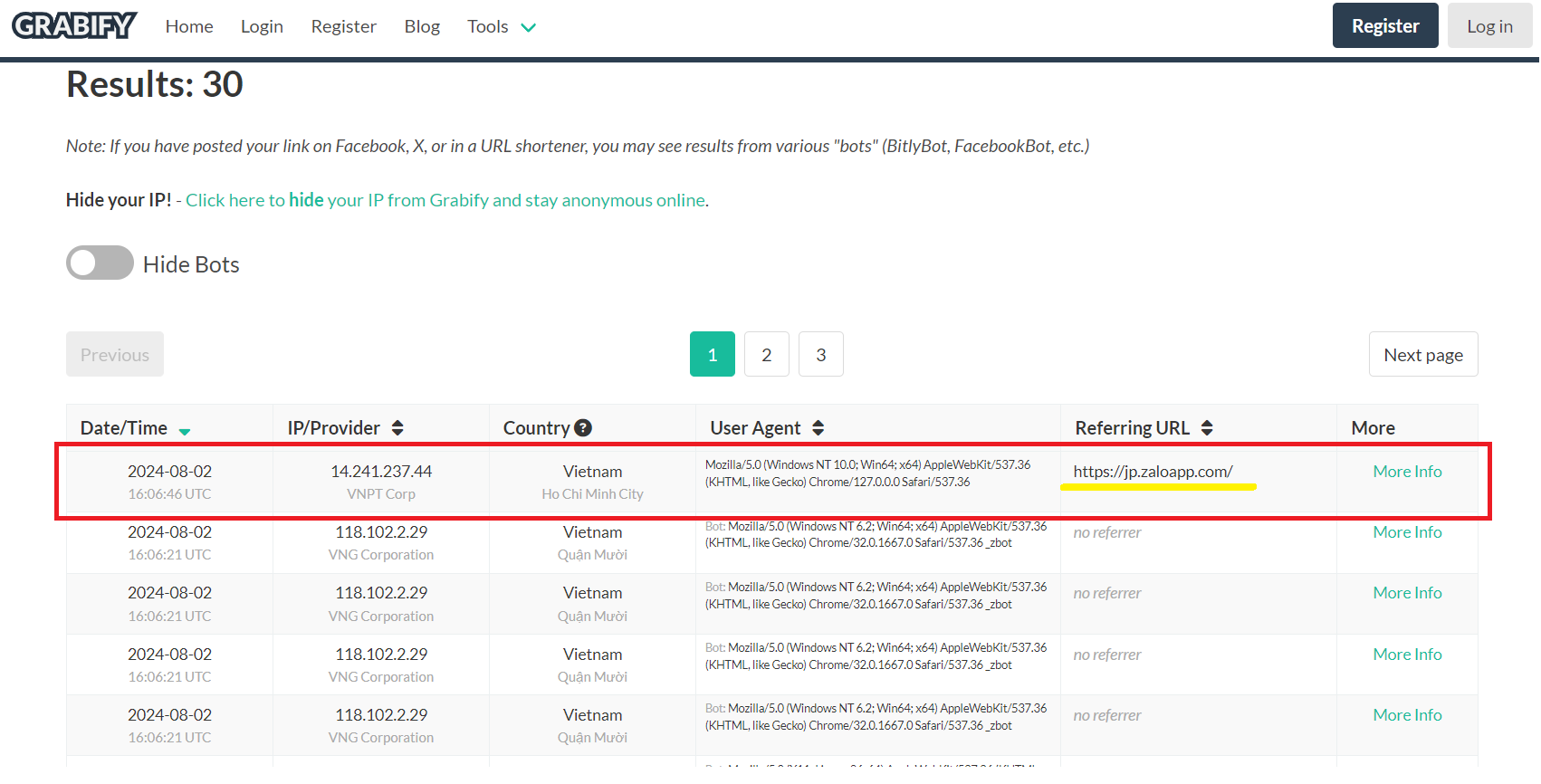
Click on to see full details.
Discover the user’s IP address using Telegram.
Introduction
Telegram, a popular messaging app, can unintentionally leak your IP address if you add a hacker to your contacts and accept a phone call from them. This vulnerability is identified as CVE-2018-17780:
- Affected Versions: Telegram Desktop (aka tdesktop) 1.3.14, and Telegram 3.3.0.0 WP8.1 on Windows.
- Vulnerability: Leaks end-user public and private IP addresses during a call due to unsafe default behavior that accepts P2P connections from clients outside of the “My Contacts” list.
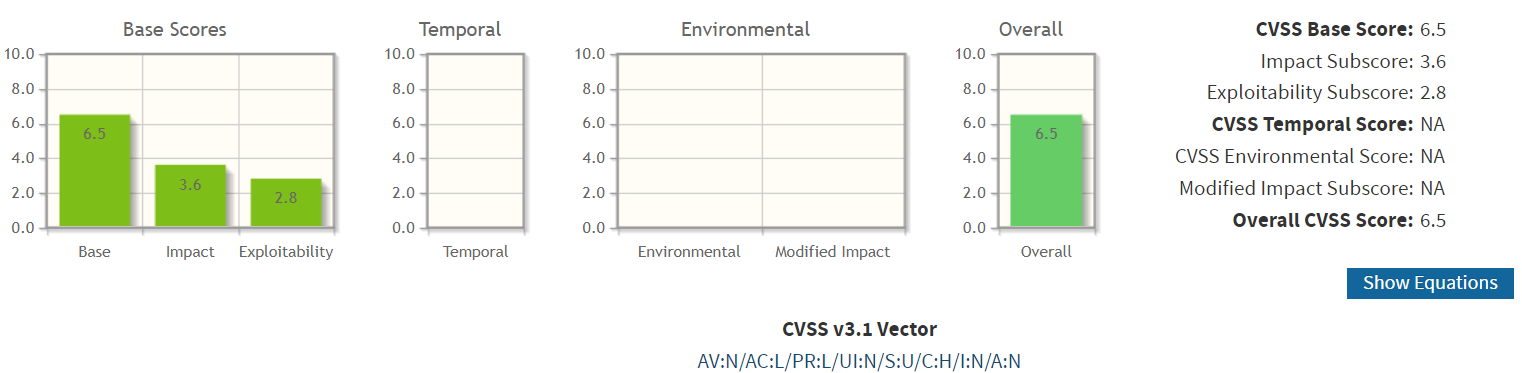
- CVSS Score: 6.5 (Medium - Version 3.x).
Unfortunately, this vulnerability still exists and continues (until now) to expose users’ IP addresses during calls.
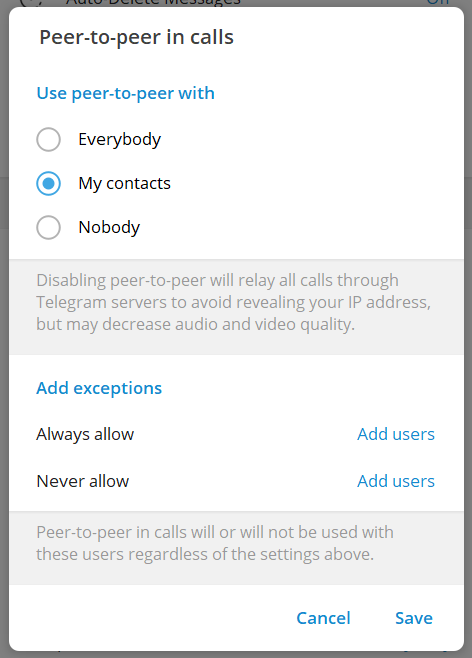
To avoid leaking your IP address while using Telegram, go to Telegram’s Settings > Privacy and Security > Calls, and then select “Never” in the Peer-to-Peer menu.
Root Cause
According to Simonov, “An unprepared person can easily reveal his IP address to his interlocutor if he does not know about them.” The reason for this leak is that Telegram, by default, uses a peer-to-peer (P2P) connection between callers for better quality and reduced latency. A Telegram spokesperson, Remi Vaughn, explained, “The downside of this is that it necessitates that both sides know the IP address of the other (since it is a direct connection). Unlike on other messengers, calls from those who are not your contact list will be routed through Telegram’s servers to obscure that.”
Proof of Concept
Step 1: Establishing the Scenario
- Add the Hacker to Contacts: The attacker persuades the victim to add them to their Telegram contacts, potentially through social engineering techniques or by impersonating a known contact.
- Initiate a Call: The attacker initiates a voice or video call to the victim using Telegram. The call request appears legitimate to the victim, who subsequently accepts the call.
Step 2: Capture Network Traffic
- Open Wireshark: The attacker opens Wireshark, a network protocol analyzer, to monitor the network traffic during the call.
- Filter for STUN Traffic: The attacker sets a filter in Wireshark to capture STUN (Session Traversal Utilities for NAT) traffic. STUN is a protocol used by Telegram for establishing peer-to-peer connections.
Step 3: Identify the IP Address
- Monitor the Call: While the call is in progress, the attacker closely monitors the STUN traffic in Wireshark for any packets containing IP address information.
- Extract the IP Address: Upon detecting the relevant STUN packets, the attacker analyzes the packet details to extract the victim’s public IP address. This information is now accessible to the attacker.
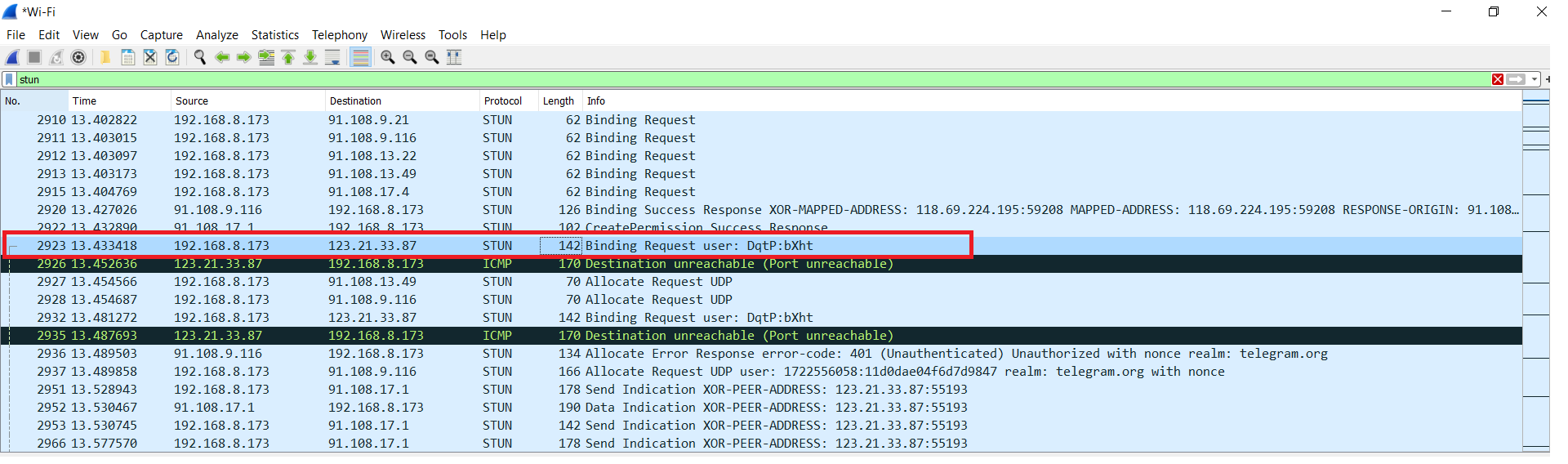
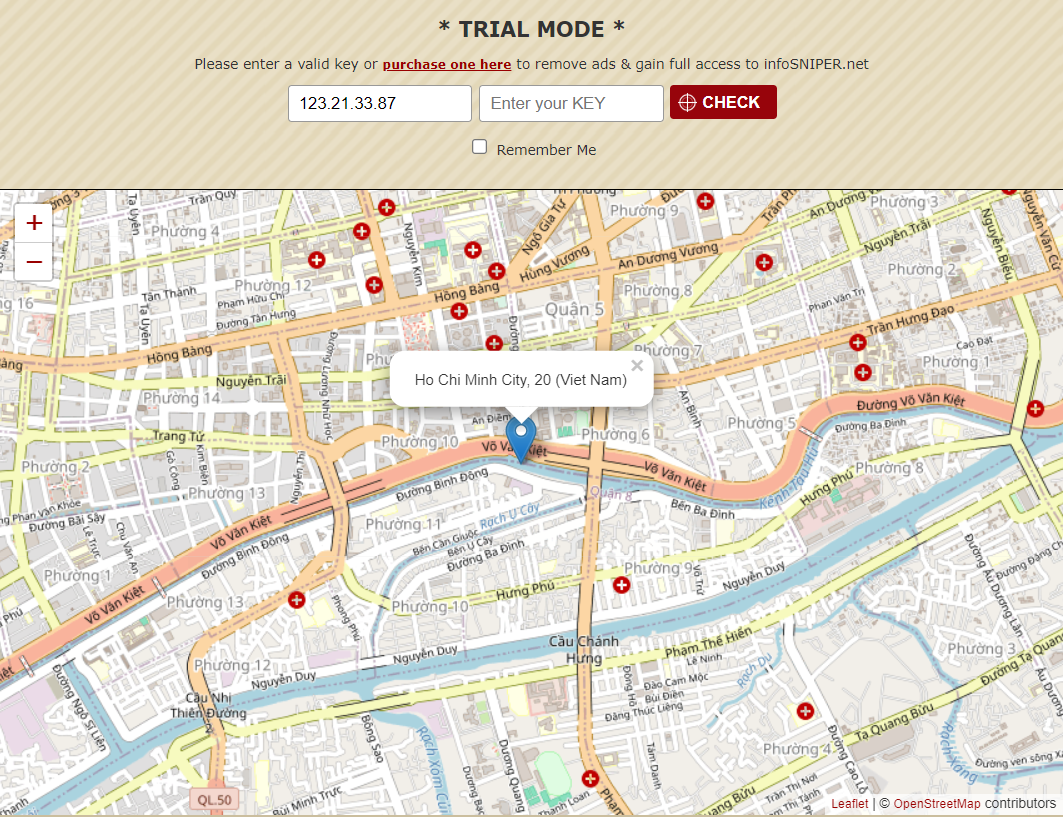
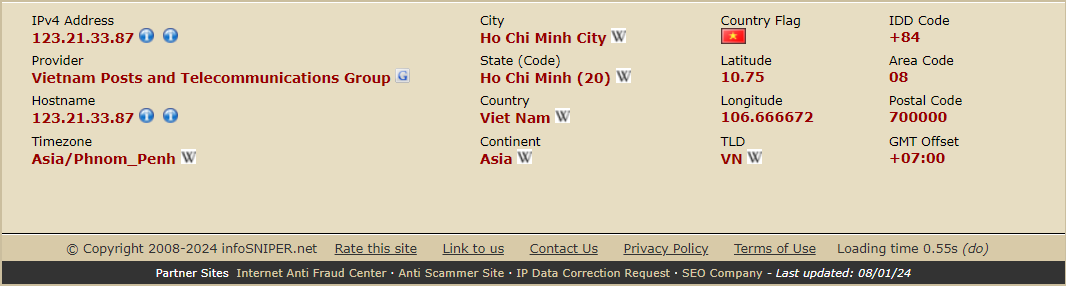
With the IP address in hand, you can use a web service like InfoSniper to find the location associated with the IP address.
Conclusion
Understanding the methods cybercriminals use to extract IP addresses through chat applications like Zalo and Telegram is crucial in today’s digital landscape. By highlighting the tactics of URL spoofing and phishing, as well as exposing vulnerabilities within these platforms, I hope to raise awareness about the potential risks and encourage proactive measures for online safety. Always be vigilant when interacting with links and unknown contacts, and take advantage of privacy settings to protect your personal information. Staying informed and cautious is your best defense against cyber threats.
Stay safe, and keep your data secure!
References
- Kennedy Muthii. (2024, January 1). How to track IP address using an image. Retrieved from https://www.golinuxcloud.com/track-ip-address-using-an-image/
- Lorenzo Franceschi-Bicchierai. (2023, October 19). Telegram is still leaking user IP addresses to contacts. TechCrunch. Retrieved from https://techcrunch.com/2023/10/19/telegram-is-still-leaking-user-ip-addresses-to-contacts/
- Jomilė Nakutavičiūtė. (2024, January 2). URL Spoofing: Definition and explanation. Retrieved from https://nordvpn.com/blog/url-spoofing/
- CyStack. (n.d.). Phishing là gì? Cách phòng chống tấn công Phishing hiệu quả. Retrieved from https://cystack.net/blog/phishing-la-gi
- National Vulnerability Database. (2018). CVE-2018-17780. Retrieved from https://nvd.nist.gov/vuln/detail/CVE-2018-17780
- Catalin Cimpanu. (2018, Septemper 29). Telegram fixes IP address leak in desktop client. ZDNet. Retrieved from https://www.zdnet.com/article/telegram-fixes-ip-address-leak-in-desktop-client/
Connect with Me
Connect with me on Facebook, LinkedIn, via email at dangduongminhnhat2003@gmail.com, GitHub, or by phone at +84829258815.