Posted on: October 7, 2024 | Reading time: 15 minutes | Word count: 3129 words | Author: Dang Duong Minh Nhat
As I explore the exciting realm of zkEVM (Zero-Knowledge Ethereum Virtual Machine), it becomes imperative to build a strong foundational understanding of key blockchain concepts. Having previously written about Zero-Knowledge Proofs (ZKPs), I recognize that knowledge of Merkle trees, Ethereum’s architecture, and the Ethereum Virtual Machine (EVM) is essential for grasping the intricacies of zkEVM. This blog serves as a comprehensive guide through the pivotal elements of blockchain technology, from the security of Merkle trees to the powerful capabilities of smart contracts on Ethereum.
Table of Contents
- Table of Contents
- Understanding Merkle Trees: The Backbone of Efficient Data Verification
- Exploring Merkle Proofs: Ensuring Data Integrity in a Decentralized World
- Understanding Blockchain: The Technology Behind Decentralization
- Exploring Ethereum: The Blockchain with a Built-in Computer
- Understanding Ether: The Heart of Ethereum’s Economy
- Unlocking the Power of Smart Contracts: The Future of Automated Agreements
- Understanding the Ethereum Virtual Machine (EVM): The Heart of Ethereum
- References
- Connect with Me
Understanding Merkle Trees: The Backbone of Efficient Data Verification
In the realm of cryptography and computer science, the Merkle tree—also known as a hash tree—stands out as a revolutionary data structure that enhances both security and efficiency in data verification. This innovative concept, patented by Ralph Merkle in 1979, has become a cornerstone for many modern cryptographic protocols, including blockchain technologies.
What is a Merkle Tree?
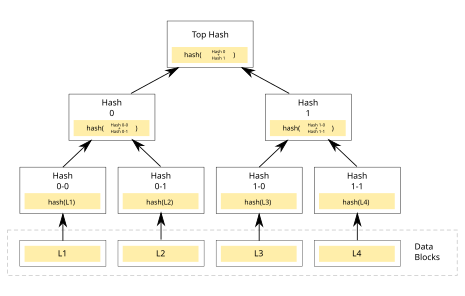
At its core, a Merkle tree organizes data in a hierarchical structure. Every “leaf” node in this tree is associated with the cryptographic hash of a specific data block. The nodes that aren’t leaves, often referred to as branch nodes, inner nodes, or inodes, hold the cryptographic hashes of their child nodes. This structure allows us to efficiently verify the integrity of large datasets.
For example, consider a Merkle tree with leaf nodes $L_1, L2, \dots, L_n$ representing individual data blocks. The tree’s structure can be visually represented as follows:
Root
/ \
Hash1 Hash2
/ \ / \
Hash3 Hash4 Hash5 Hash6
| | | |
L1 L2 L3 L4
Each parent node’s hash is computed by hashing the concatenated hashes of its child nodes. For example: $$H(\text{Hash3}, \text{Hash4}) = \text{Hash1}$$ This hierarchical organization not only optimizes data storage but also facilitates quick verification.
The Efficiency of Verification
One of the most compelling features of Merkle trees is their efficiency in verifying data inclusion. To prove that a particular leaf node (let’s say $L_i$) is part of the Merkle tree, you only need to compute a number of hashes proportional to the logarithm of the total number of leaf nodes, specifically $O(\text{log }n)$. This is significantly more efficient than a hash list, where the verification process scales linearly with the number of leaf nodes, requiring $O(n)$ computations.
Cryptographic Commitment
Merkle trees serve as effective cryptographic commitment schemes. The root hash of the Merkle tree acts as a commitment to the entire dataset, ensuring that the individual leaf nodes can later be revealed and verified as part of the original commitment. This property is essential in various applications, particularly in blockchain technology, where data integrity and security are paramount.
Exploring Merkle Proofs: Ensuring Data Integrity in a Decentralized World
In the age of digital data, ensuring the integrity and inclusion of information is more critical than ever. This is where Merkle proofs come into play, offering a powerful cryptographic method to verify whether a specific piece of data belongs to a Merkle tree. But what exactly are Merkle proofs, and how do they function? Let’s delve into the details!
What Are Merkle Proofs?
Merkle proofs are cryptographic techniques designed to validate the inclusion of specific data within a larger dataset represented by a Merkle tree. They allow users to confirm that a data element is part of the tree without needing access to the entire dataset, thus ensuring both security and efficiency.
Key Uses of Merkle Proofs
- Data Inclusion Verification: Merkle proofs confirm whether a particular data element is part of a given Merkle tree, providing assurance about the data’s authenticity.
- Efficient Data Validation: These proofs enable the validation of data inclusion in a larger dataset without exposing unnecessary information or requiring access to the full dataset.
- Secure Verification: By utilizing cryptographic techniques, Merkle proofs ensure that the verification process remains secure, protecting sensitive data from exposure.
How Do Merkle Proofs Work?
At the heart of Merkle proofs is the reliance on one-way hashing functions. These functions are crucial because they are collision-resistant and deterministic; no two different pieces of data should produce the same hash, and the same data will always yield the same hash.
To establish a Merkle proof, the process involves hashing the corresponding hashes of sibling nodes and traversing up the tree until reaching the root hash, which is publicly known. This root hash serves as the ultimate verification point, confirming the inclusion of the original data without revealing it.
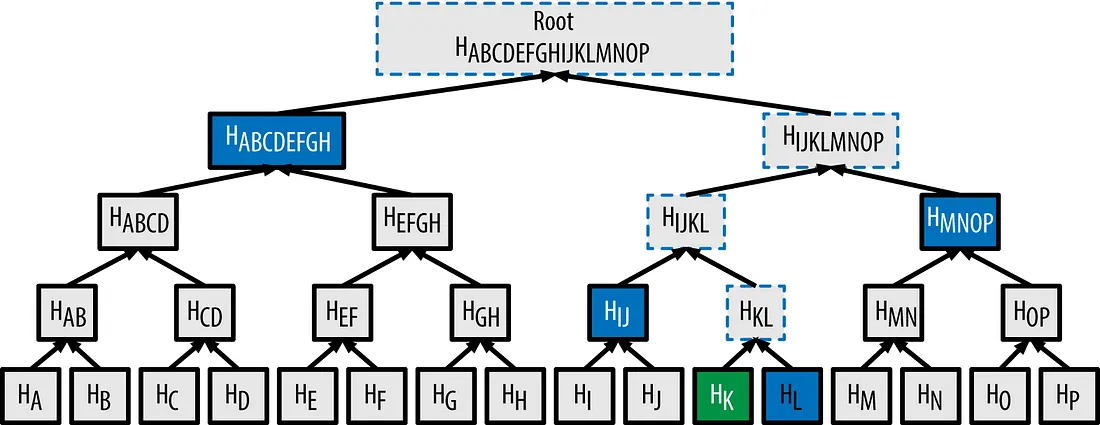
Step-by-Step Example of a Merkle Proof
Let’s consider a practical example to illustrate how Merkle proofs work. Imagine we want to verify the inclusion of a data element $K$ in a Merkle tree:
- Hashing the Data: First, we hash the data $K$ using a one-way function to obtain $H(K)$.
- Combining Hashes: Next, we combine $H(K)$ with the hash of another dataset $L$, resulting in $H(KL)$.
- Continuing the Process: This combined hash $H(KL)$ is then hashed with another hash $H(IJ)$, leading to $H(IJKL)$.
- Climbing Up the Tree: We continue this process, combining hashes up the tree:
- $H(IJKL)$ is hashed with $H(MNOP)$ to produce $H(IJKLMNOP)$.
- Finally, $H(IJKLMNOP)$ is hashed with $H(ABCDEFGH)$ to produce the Merkle root $H(ABCDEFHGIJKLMNOP)$.
By utilizing the hashes $H(L)$, $H(IJ)$, $H(MNOP)$, and $H(ABCDEFGH)$, we can conclusively prove that the data element $K$ is indeed part of the Merkle tree, all without revealing $K$ or any other data within the tree.
Applications of Merkle Proofs
Merkle proofs are vital in various applications, especially within blockchain technology. They play a crucial role in:
- Proving Data Inclusion: Enabling users to demonstrate that specific data is part of a larger dataset, enhancing trust and transparency.
- Ensuring Data Integrity: Providing a mechanism to verify that data has not been altered or tampered with.
- Facilitating Secure and Efficient Validation: Supporting distributed systems where data must be validated quickly and securely without compromising privacy.
Understanding Blockchain: The Technology Behind Decentralization
In recent years, the term “blockchain” has surged into the spotlight, often associated with cryptocurrencies like Bitcoin and Ethereum. But what exactly is a blockchain, and why is it considered a revolutionary technology? Let’s break it down in an easy-to-understand way.
What Is a Blockchain?
At its core, a blockchain is a public database that is maintained and updated across a network of computers, known as nodes. This decentralized structure allows for transparency and security in transactions, making it a crucial component of many modern technologies.
Blocks and Chains
The term “blockchain” comes from two fundamental concepts: blocks and chains.
- Blocks: Each block in a blockchain contains data related to transactions, such as timestamps, sender and receiver information, and amounts transferred. When you send Ethereum (ETH) to someone, the transaction details are bundled into a block for it to be processed successfully.
- Chain: Each block is cryptographically linked to its predecessor, forming a chain. This means that if you want to alter any data in a block, you would have to change every subsequent block in the chain, which is nearly impossible without the consensus of the entire network.
The Role of Nodes
Every computer participating in the blockchain network is referred to as a node. These nodes collectively ensure that everyone interacting with the blockchain has a consistent and identical copy of the data. This distributed agreement is essential for maintaining the integrity of the blockchain.
To achieve this consensus, blockchains rely on specific mechanisms, which can vary between different blockchain systems.
Consensus Mechanisms: Proof of Stake
Ethereum, one of the most well-known blockchain platforms, employs a consensus mechanism called Proof of Stake (PoS). Here’s how it works:
- Staking: Anyone wishing to add new blocks to the chain must stake ETH, the native currency of Ethereum, as collateral. This staking process aligns the interests of the validators with the network’s security.
- Validators: Participants who stake their ETH can become validators. These validators are randomly selected to propose new blocks based on the amount they have staked. This system incentivizes them to act honestly because dishonest behavior could result in the loss of their staked ETH.
- Verification and Rewards: Once a validator proposes a block, other validators check its accuracy. If the block is accepted, the validator receives a reward in ETH. Conversely, validators who act maliciously face penalties, which reinforces the need for honest participation.
Exploring Ethereum: The Blockchain with a Built-in Computer
In the ever-evolving landscape of technology, Ethereum stands out as a groundbreaking innovation that has transformed the way we think about applications and organizations. But what exactly is Ethereum, and how does it work? Let’s dive into the intricacies of this unique blockchain platform.
What Is Ethereum?
At its core, Ethereum is more than just a blockchain; it is a decentralized platform that allows developers to build applications and organizations without the need for centralized control. It combines the principles of blockchain technology with a robust computing environment, enabling a wide array of possibilities.
The Role of Blockchain
The results of these computations, along with a record of all transactions, are stored on the blockchain. This immutable ledger ensures that once a transaction is verified and added, it cannot be altered or deleted. Cryptographic mechanisms are in place to secure these transactions, guaranteeing that they are executed with the appropriate permissions. For instance, only Alice can send digital assets from her account, thanks to cryptographic signatures.
Security and Integrity
One of Ethereum’s key features is its focus on security. The combination of cryptographic techniques and decentralized consensus means that tampering with the blockchain is virtually impossible. This creates a trustless environment where participants can engage without needing to rely on a central authority.
Why Is Ethereum Important?
Ethereum has paved the way for a new era of decentralized applications (dApps) and organizations. Its ability to execute smart contracts—self-executing contracts with the terms of the agreement directly written into code—opens up endless possibilities for innovation across various sectors, including finance, healthcare, and supply chain management.
Understanding Ether: The Heart of Ethereum’s Economy
In the intricate ecosystem of Ethereum, one cryptocurrency stands out as the lifeblood of its decentralized network: Ether (ETH). But what exactly is Ether, and what role does it play in the broader Ethereum landscape? Let’s explore its significance, functionality, and the innovative economic model that underpins it.
What Is Ether?
Ether (ETH) is the native cryptocurrency of the Ethereum platform, designed not just as a digital currency but as a means to facilitate transactions and computations within this decentralized environment. Its primary purpose is to create a market for computation, providing incentives for participants to verify and execute transaction requests.
How Does Ether Work?
Whenever a participant wants to execute a transaction, they must include a certain amount of Ether as a bounty. This bounty serves several essential functions:
- Incentive Structure: By requiring a fee in ETH, the network incentivizes users to verify and execute transactions. This ensures that only those who are willing to contribute resources to the network will be able to submit transaction requests.
- Resource Allocation: The amount of ETH paid corresponds to the computational resources required for the task. More complex transactions require higher fees, which effectively allocates network resources based on demand.
- Deterrent Against Abuse: To prevent malicious users from clogging the network with excessive or resource-intensive requests, the system mandates that participants pay for computation. This mechanism acts as a safeguard, ensuring that the network remains efficient and responsive.
How Ether Secures the Network
Beyond its role as a medium for transaction fees, Ether provides crypto-economic security to the Ethereum network in three key ways:
- Rewards for Validators: Ether is used to reward validators who propose new blocks or expose dishonest behavior within the network. This reward system encourages active participation and integrity among validators.
- Staking and Collateral: Validators must stake a portion of their ETH, which acts as collateral. If they attempt to act maliciously or violate network rules, their staked ETH can be destroyed. This mechanism fosters honesty and accountability.
- Voting Mechanism: Ether is also utilized to weigh votes for newly proposed blocks, contributing to the consensus mechanism. This ensures that the network can achieve agreement on the state of the blockchain, further enhancing its security and reliability.
Unlocking the Power of Smart Contracts: The Future of Automated Agreements
In the ever-evolving landscape of blockchain technology, smart contracts emerge as a revolutionary concept that transforms how we conduct transactions and agreements. But what exactly are smart contracts, and how do they work within the Ethereum ecosystem? Let’s dive into their intricacies, functionalities, and the exciting possibilities they offer.
What Are Smart Contracts?
At their core, smart contracts are self-executing scripts stored and executed on the Ethereum Virtual Machine (EVM). Unlike traditional contracts that require human oversight, smart contracts automatically enforce and execute the terms of an agreement when predefined conditions are met. Think of them as digital vending machines: once you input the right parameters (like sending Ether), the machine dispenses the desired outcome—whether that be a digital asset, access to a service, or a specific computation.
How Do Smart Contracts Work?
Smart contracts are essentially reusable code snippets uploaded by developers to the EVM. Here’s how the process unfolds:
- Creation and Upload: Developers create smart contracts—pieces of code that encapsulate business logic or transactions—and upload them to the Ethereum blockchain. This process involves a small fee paid in Ether, which incentivizes the network to maintain and execute these contracts.
- Execution on Request: Users can interact with these contracts by sending requests with various parameters. Each request triggers the contract’s execution, allowing users to perform a wide range of actions without needing to write new code each time.
- Condition-Based Actions: The smart contract then evaluates the inputs against its programmed conditions. If the conditions are satisfied, the contract executes the specified actions automatically. For instance, a simple vendor smart contract may transfer ownership of a digital asset if the caller sends a specified amount of Ether to the contract.
The Benefits of Smart Contracts
The advantages of smart contracts are manifold:
- Transparency and Trust: Since the code is publicly available on the blockchain, all parties can verify the terms and conditions, fostering trust and transparency.
- Efficiency and Speed: By automating execution, smart contracts eliminate the need for intermediaries, significantly speeding up transaction processes and reducing costs.
- Security: Smart contracts leverage cryptographic principles, making them tamper-proof and resistant to fraud.
- Versatility: Developers can create a wide array of applications using smart contracts, from decentralized finance (DeFi) solutions and marketplaces to games and social networks.
Understanding the Ethereum Virtual Machine (EVM): The Heart of Ethereum
In the realm of blockchain technology, the Ethereum Virtual Machine (EVM) stands out as a groundbreaking component that powers the entire Ethereum network. Acting as a decentralized environment, the EVM executes smart contracts in a secure and consistent manner across all Ethereum nodes. Let’s unravel the complexities of the EVM and understand its crucial role in the Ethereum ecosystem.
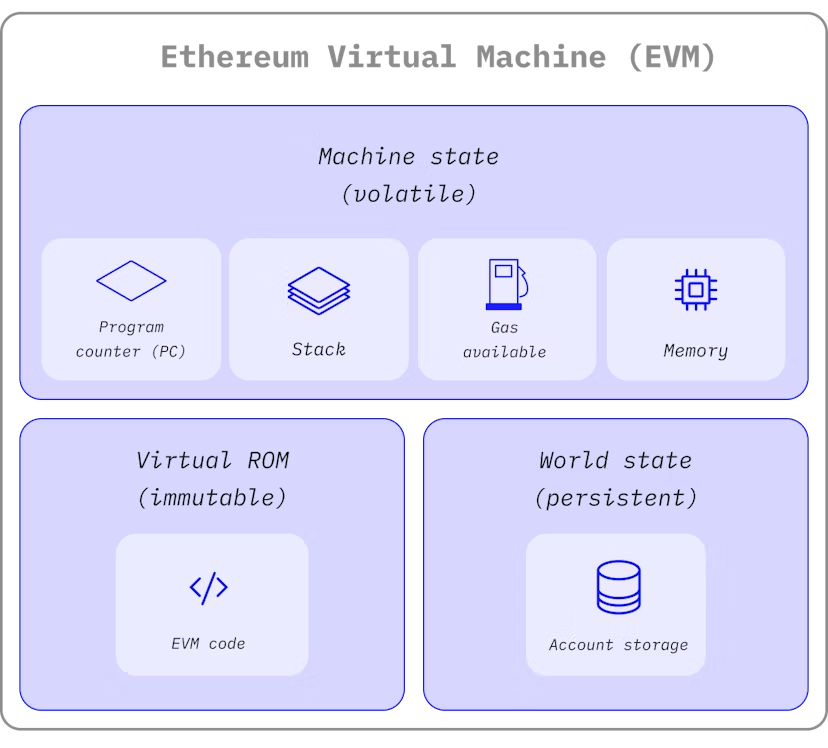
What is the EVM?
At its core, the EVM is a distributed state machine that processes transactions and maintains the state of the Ethereum network. Unlike a simple distributed ledger, which records transactions like Bitcoin, the EVM allows for dynamic interactions through smart contracts—essentially self-executing agreements with the terms directly written into code.
The State Transition Function
The EVM operates using a mathematical function known as the state transition function. This function can be expressed as: $$Y(S, T) = S’$$ Where:
- $S$ = Old valid state of the Ethereum network
- $T$ = New set of valid transactions
- $S’$ = New valid state after the transactions are processed
This deterministic nature means that given a specific input (old state and transactions), the output (new state) is predictable and consistent.
The Structure of State
The state of the Ethereum network is represented by a complex data structure known as a modified Merkle Patricia Trie. This structure allows for efficient storage and retrieval of account information, with all accounts linked by hashes and reducible to a single root hash stored on the blockchain.
Types of Transactions
Transactions in Ethereum can be categorized into two types:
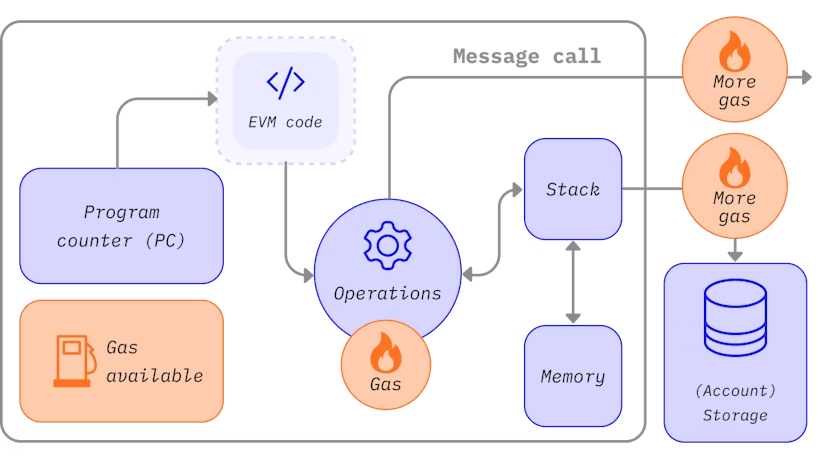
- Message Calls: Instructions that invoke functions in existing smart contracts.
- Contract Creation: Transactions that create new contract accounts containing compiled smart contract bytecode.
When another account calls a contract, the EVM executes the contract’s bytecode, changing the state based on the logic defined within the smart contract.
EVM Instructions
The EVM operates as a stack machine with a depth of 1024 items, where each item is a 256-bit word. This word size aligns with modern cryptographic standards, making operations efficient and secure. During execution, the EVM uses a transient memory structure that does not persist between transactions.
Smart contracts execute as a series of EVM opcodes, performing standard operations like ADD, SUB, XOR, and blockchain-specific functions such as ADDRESS and BALANCE.
Gas: The Fuel of the EVM
To ensure efficient resource allocation, the EVM uses a mechanism known as gas. Gas measures the computational effort required for operations, preventing abuse and ensuring that participants pay for the resources they consume. Each operation in the EVM has a specific gas cost associated with it, which users must account for when submitting transactions.
EVM Implementations
The EVM has evolved over the years, leading to various implementations across different programming languages. Some notable implementations include:
- Py-EVM (Python)
- evmone (C++)
- ethereumjs-vm (JavaScript)
- revm (Rust)
All implementations adhere to the specifications outlined in the Ethereum Yellowpaper, ensuring consistency across the network.
References
- Merkle tree. Wikipedia. Retrieved from: https://en.wikipedia.org/wiki/Merkle_tree
- Belavadi Prahalad. (2018, January 7). Merkle proofs Explained. Retrieved from: https://medium.com/crypto-0-nite/merkle-proofs-explained-6dd429623dc5
- Intro to Ethereum. Ethereum. Retrieved from: https://ethereum.org/en/developers/docs/intro-to-ethereum/
- Ethereum Virtual Machine (EVM). Ethereum. Retrieved from: https://ethereum.org/en/developers/docs/evm/
Connect with Me
Connect with me on Facebook, LinkedIn, via email at dangduongminhnhat2003@gmail.com, GitHub, or by phone at +84829258815.